How CloudTruth Works
/CT-Misconfiguration-Solution-Main-Graphic-Steps-v1.png?width=1000&height=700&name=CT-Misconfiguration-Solution-Main-Graphic-Steps-v1.png)

NSA / CISA Warning on Misconfigurations
The recent advisory from the NSA and CISA sheds light on prevalent misconfigurations in many organizations, serving as a crucial reminder for DevOps professionals to bolster security measures.
These insights are not merely a call to action but a roadmap for integrating robust security measures within the DevOps lifecycle. Notably, the advisory advocates for:
- Removing default credentials
- Automating patching
- Enforce multi-factor authentication (MFA)
Master your Input Variables
One of the most challenging DevOps tasks is getting config and secrets "just right" for every component in your system.
Whether that's config for infrastructure or applications, generating a consistently perfect config file is a real challenge.
In this video, we dive into how CloudTruth avoids misconfigurations with a new way to manage input variables.

Top 3 Reasons Misconfigurations Slow Deployment Velocity
Misconfigurations are literally 100% of the reason why things go wrong. Whether it's from a security perspective, an infrastructure perspective or a simple accidental button click.
When you try to deploy an application and it fails, what's the reason? Misconfigurations.
From a security perspective, Red Hat states in the State of Kubernetes and Container Security report, 70% of security vulnerabilities were due to misconfigurations.
Most of the time, these misconfigurations happen because of a wrong button click, or someone accidentally put the wrong value into a variable or a parameter. Although mistakes happen, a lot of them can be avoided.
Learn More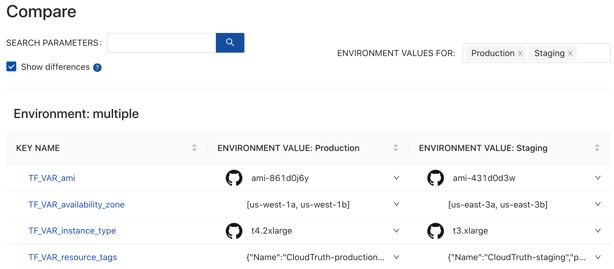
What's Different Between Staging and Prod?
- All config with versioned history
- Solve outages faster
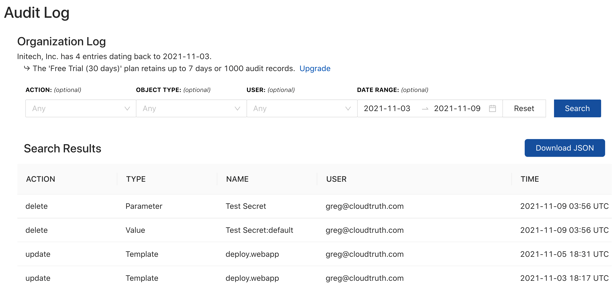
Quickly Identify Config Changes
- Track who, when, and previous values
- Rollback changes
- Granular RBAC controls
- Kubernetes secrets rotation
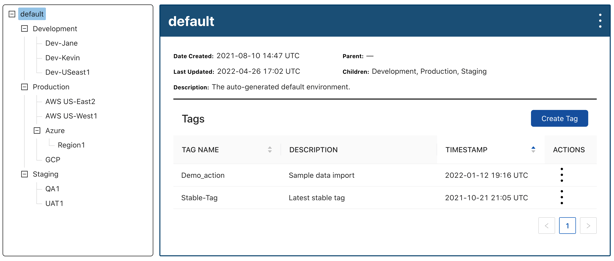
Keep Your Config DRY
- Discover a better way to manage all your input variables for infrastructure and apps.
- Inject perfect config and secrets into CI/CD for build, deploy, and runtime workflows.

What's Different Between Staging and Prod?
- All config with versioned history
- Solve outages faster

Quickly Identify Config Changes
- Track who, when, and previous values
- Rollback changes
- Granular RBAC controls
- Kubernetes secrets rotation

Keep Your Config DRY
- Discover a better way to manage all your input variables for infrastructure and apps.
- Inject perfect config and secrets into CI/CD for build, deploy, and runtime workflows.
Print Perfect Config
.png?width=500&name=CT%20Logo-Horizontal%20(medium).png)


/CT-Hero-Misconfiguration-Solution-Text-Animation-Oct23-370x100-v3.gif)