What is an Audit Trail?
Audit trails chronologically record system-wide events and user activities to ensure a historical record is available for security and operational review, often for compliance requirements or internal investigations.
These records provide auditors with proof of compliance and operational integrity. Most compliance framework security controls require some type of audit trail to ensure a verifiable historical is accessible to auditors.
Audit trails are tamper-proof and not able to be manipulated by users of the system being audited. This is typically managed by the technology vendor as core functionality for any platform that is managing important data.
Auditing vs. Logging
It’s important to differentiate between a logging system and an audit trail for compliance. The two concepts complement each other. Logging refers to capturing system technical operation details for performance profiling and error tracking. An audit trail is designed to record user activity within the system, such as “create”, “delete” and “update” actions, and access rights permissions changes.
Logging systems do not need tamper-proof designs since most logs are stored as formatted text files. Logging does not typically have the data retention requirements compared to audit logs. Auditing systems employ measures to ensure records can’t be altered and the data is often stored in a database as compared to text files.
Why is it useful?
Nearly every enterprise SaaS requires audit trail functionality to support security and compliance requirements. These systems need to capture all activity from the API, CLI or GUI interfaces.
An auditing feature should allow interactive search by user, date, activity, and data type. The data should also be exportable in an easy-to-share format such as JSON or CSV.
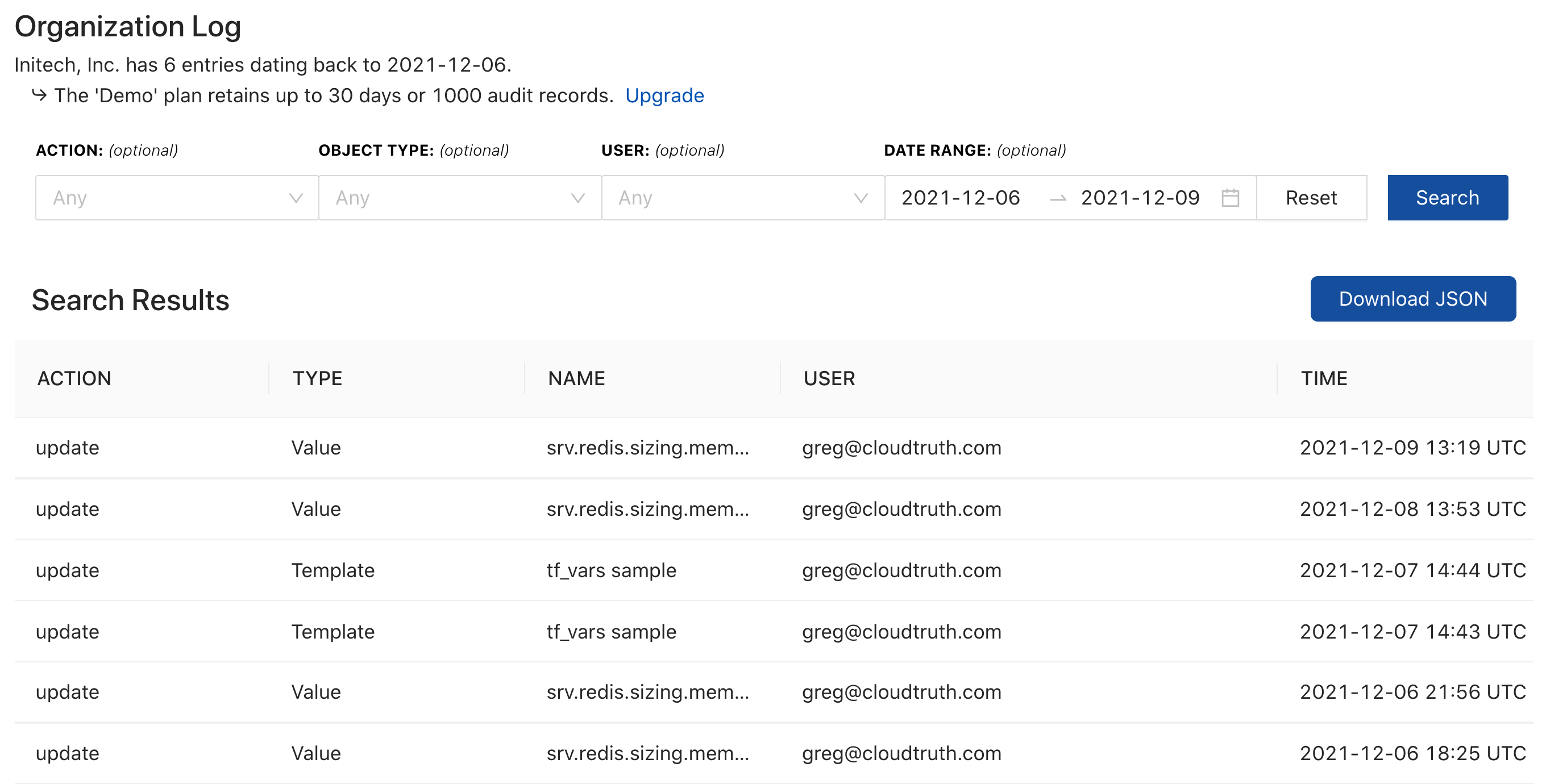
The CloudTruth Audit Log is built into the core platform and is a requirement for any unified configuration management system.
Below is the CloudTruth audit trail feature showing the interactive search and JSON download capabilities.
Join ‘The Pipeline’
Our bite-sized newsletter with DevSecOps industry tips and security alerts to increase pipeline velocity and system security.