
Argo CD is a tool that allows you to deploy and manage Kubernetes resources as part of your GitOps workflows. Separating config data from source code is a best practice from Argo and a factor when developing a twelve-factor app. We are going to review how to manage your secrets and config outside of your source code with the CloudTruth Argo CD plugin.
Managing secrets with the Argo CD plugin
The CloudTruth Argo CD plugin will replace secrets and config data within Kubernetes YAML files using <> as a template format. When creating K8s secrets with the plugin, a secrets yaml using stringData would look like the following:
apiVersion: v1 kind: Secret metadata: name: cloudtruth-secret type: Opaque stringData: password: <cloudtruth-secret>
The CloudTruth plugin substitutes the value for cloudtruth-secret since it is specified within the <> markers. The value will be retrieved from your CloudTruth organization’s managed vault for the project and environment you specify.
Installing the CloudTruth Argo CD plugin
The first step to managing secrets is installing the CloudTruth Argo CD plugin. We provide a quick getting started script which allows you to specify a set of base CloudTruth Parameters for authentication and config.
curl -s https://raw.githubusercontent.com/cloudtruth/argocd-cloudtruth-plugin/main/install/setup.sh | sh
You can provide the installer with the following parameter values:
| Parameter | Value |
| CLOUDTRUTH_API_KEY | Provides access to your CloudTruth org |
| CLOUDTRUTH_ENVIRONMENT | Specifies a targeted Environment |
| CLOUDTRUTH_PROJECT | Specifies a targeted project |
| CLOUDTRUTH_TAG | Specifies a targeted tag |
The installer will perform the following to configure the plugin in your Argo CD installation:
- Create a K8s
secretwith the provided parameters in theargocdnamespace. - Patch the argocd configmap to add CloudTruth to
configManamentPlugins - Patch the argocd-repo-server to add the required volumes, secret and init containers.
Using the plugin for secrets and parameters
You can now reference CloudTruth config in your app config files. When creating an application from a Git repository using the Argo CD UI, plugins are enabled from the Directory dropdown.
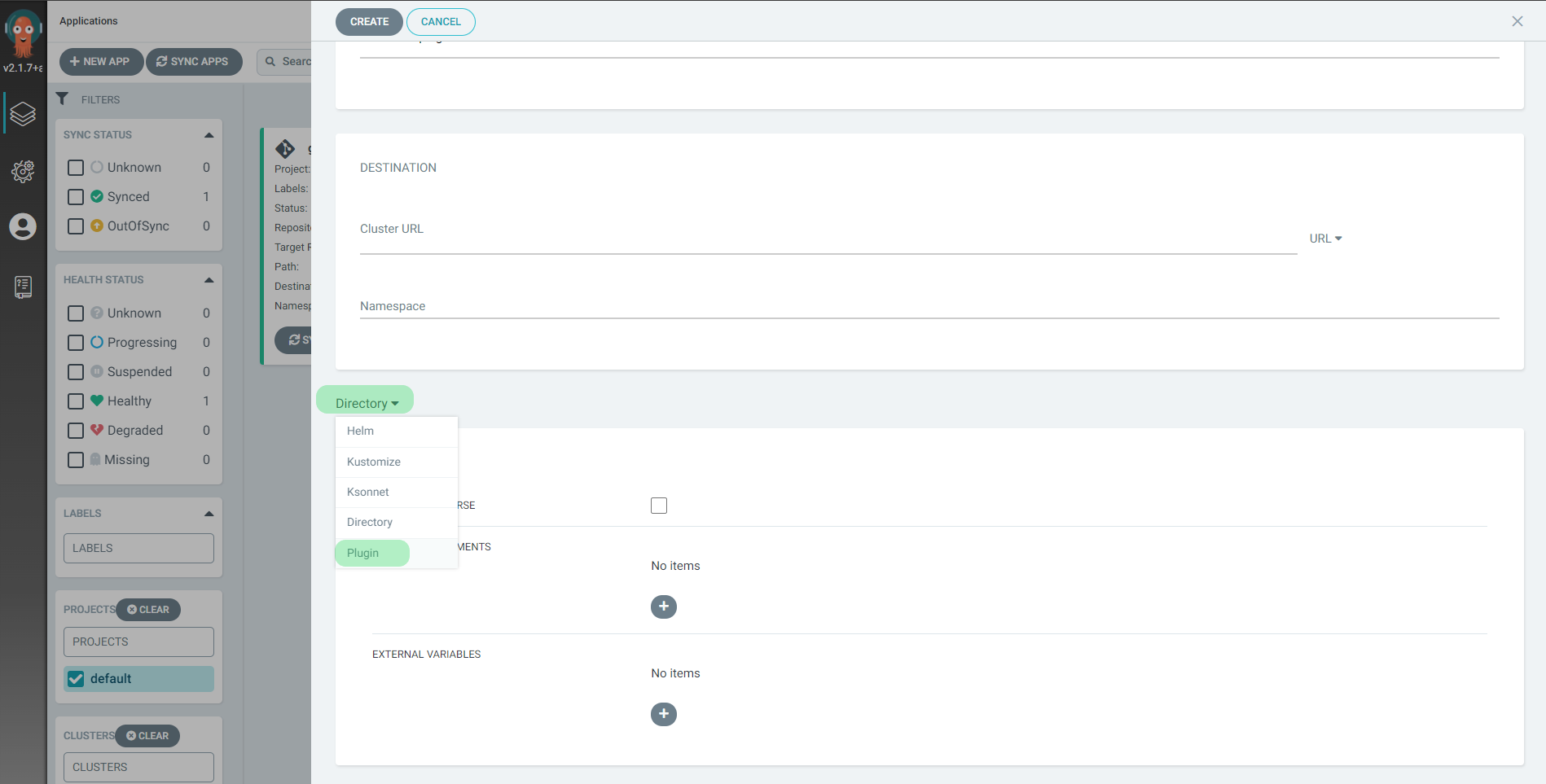
Select the argocd-cloudtruth-plugin
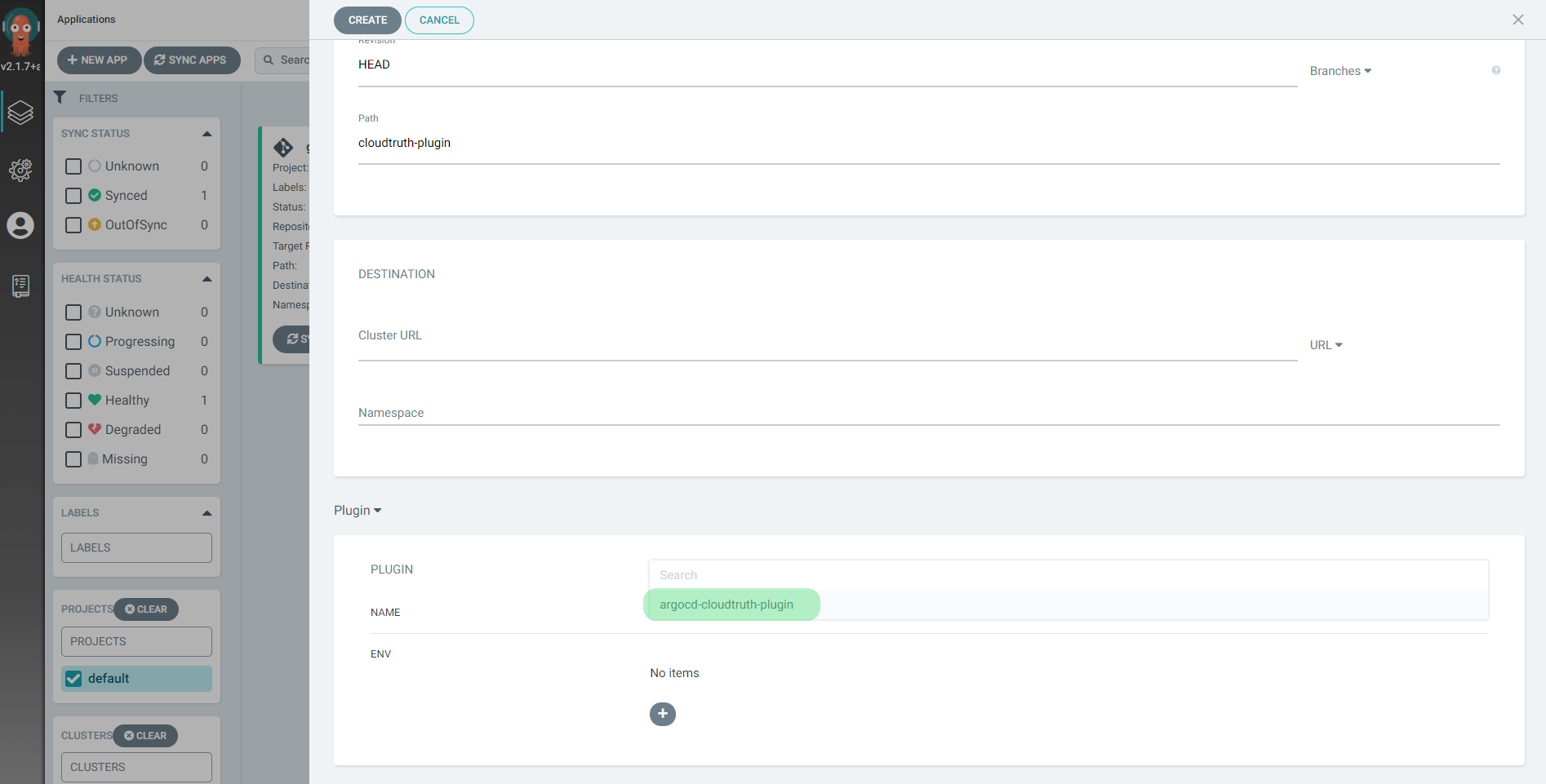
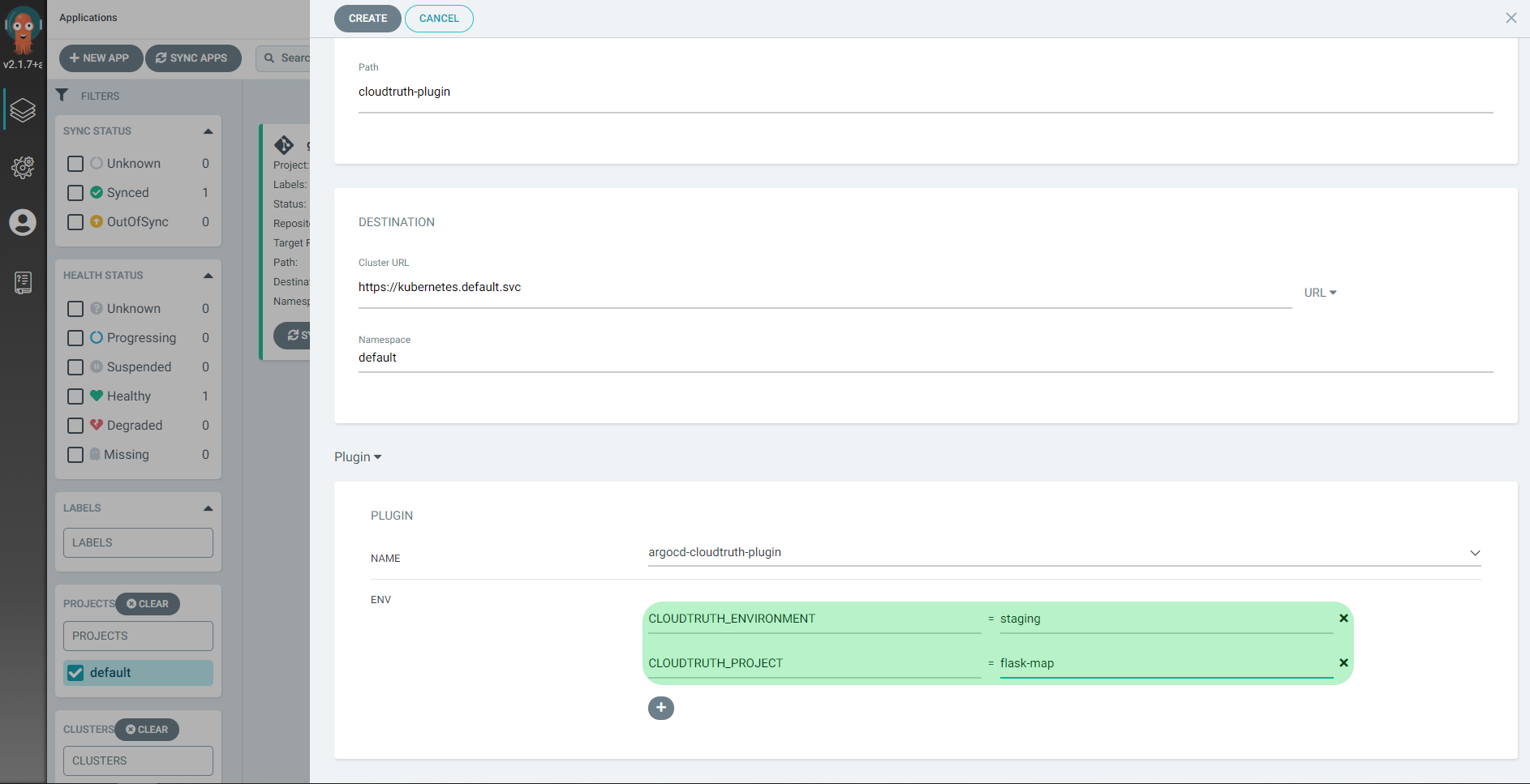
Plugin ENV values allow you to override any installation parameter values for your specific app.
Managing secrets demo with the Argo plugin
Here is an example use case with the Argo CD plugin that populates a secret and mounts that secret to a redis pod. The secret value is pulled from CloudTruth.
We will deploy the pod from our demo Git repo.
The secret password substitutes the secret from CloudTruth using the default substitution format <>.
apiVersion: v1 kind: Secret metadata: name: secret-basic-auth type: kubernetes.io/basic-auth stringData: username: admin password: <argo-secret>
You can use the CloudTruth CLI that sets up a project to deploy this example. This creates a project called argocd and creates a secret called argo-secret.
cloudtruth --project argocd set cloudtruth --project argocd parameters set argo-secret --value t0p-Secret --secret true
You can use the Argo CLI create command to deploy the app:
argocd app create cloudtruth-secret-management --repo https://github.com/cloudtruth/blog-examples --path argo-secret --dest-server https://kubernetes.default.svc --dest-namespace default --config-management-plugin argocd-cloudtruth-plugin --plugin-env CLOUDTRUTH_ENVIRONMENT=production --plugin-env CLOUDTRUTH_PROJECT=argocd
The argocd app create is broken down into the following commands. The --plugin-env flags specify the CloudTruth environment and project to get values from.
| Command | Value |
| –repo | https://github.com/cloudtruth/blog-examples |
| –path | argo-secret |
| –dest-server | https://kubernetes.default.svc |
| –dest-namespace | default |
| –config-management-plugin | argocd-cloudtruth-plugin |
| –plugin-env | CLOUDTRUTH_ENVIRONMENT=production |
| –plugin-env | CLOUDTRUTH_PROJECT=argocd |
Deploy by synching the app:
argocd app sync cloudtruth-secret-management
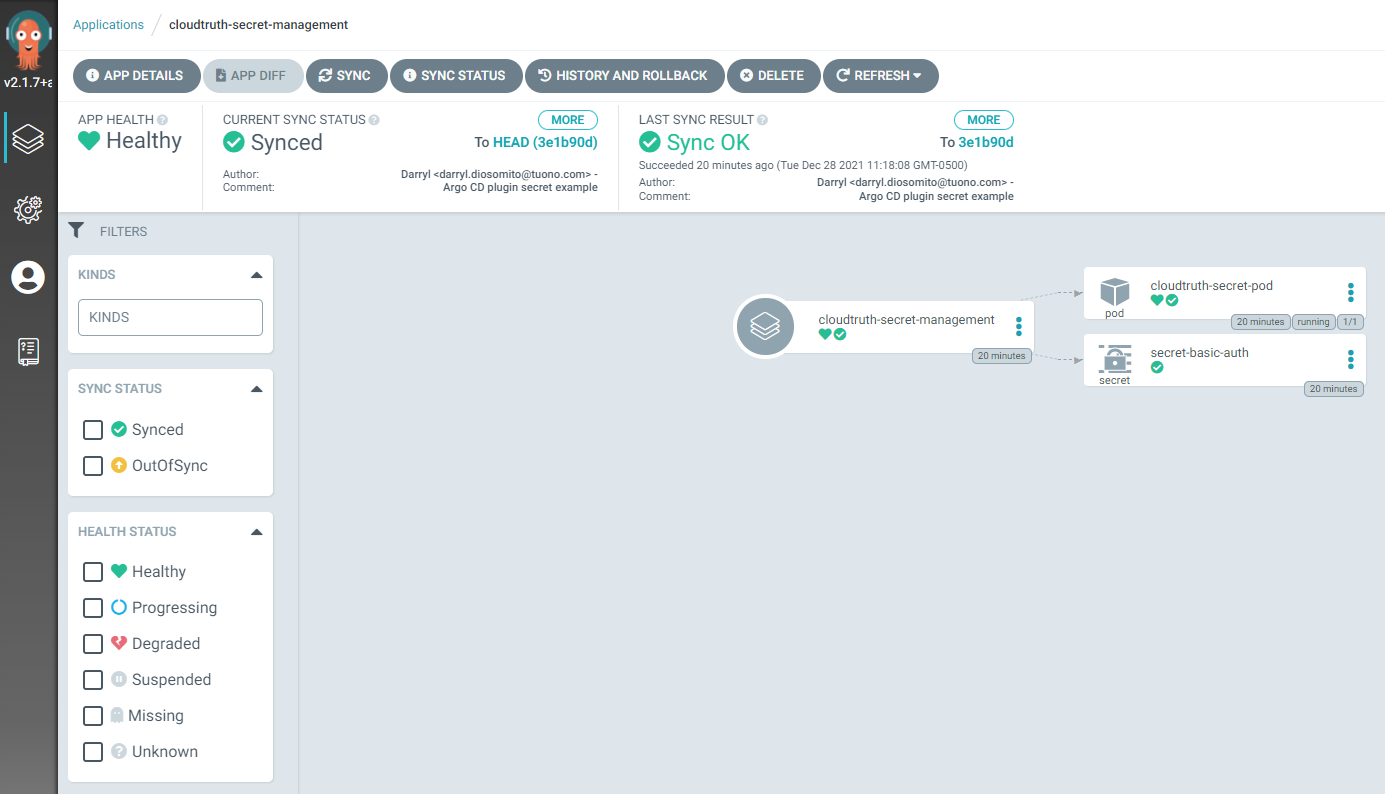
You can verify the secret value by inspecting the created kubernetes secret or exec into the pod to inspect the secret mounted as a volume.

The Argo CD UI displays the deployed pod and secret.
For additional information on the Argo CD plugin you can read the docs and check out our open source repository.
Join ‘The Pipeline’
Our bite-sized newsletter with DevSecOps industry tips and security alerts to increase pipeline velocity and system security.



