
Platform integrations, especially with the cloud, are crucial for Application Developers, DevOps, and infrastructure engineers due to the vast amount of platforms in today’s developer world. Whether it’s monitoring platforms, CICD, or even secrets, the ability to integrate into a 3rd party is crucial.
In this blog post, you’ll learn about how CloudTruth performs easy integrations with Azure and AWS along with how you can get started in a hands-on fashion right now.
Enterprise Secrets Integration For The Enterprise
Every platform, architecture, and application that teams build has some sort of secret. Whether it’s a connection string to a database, API keys for an application a secret that’s being ingested into a containerized application, or authentication/authorization to a Linux server. In any case, App Dev and DevOps teams need a way to retrieve and ingest secrets.
Let’s think about an example from a Kubernetes perspective. In any Kubernetes cluster, you have users that have access. It could be a user that has single tenancy permissions to one cluster, or it could be a multitenancy user that has access across many clusters. In any case, you need to create the user and the username gets added to the user’s Kubeconfig. That way, the user has access to the clusters. The question becomes where do I store the user’s username and password? and the answer from a cloud perspective could be AWS SSM or Secrets Manager.
With CloudTruth, you can pull the user from the above example and add it to a Kubernetes Manifest that has a RoleBinding or ClusterRoleBinding spec and ensure that the information that’s being passed in is secure.
The AWS Method
In this section, you’ll learn how to set up the integration between CloudTruth and AWS to retrieve, or write, information from SSM, Secrets Manager, and S3.
Log into the CloudTruth portal and go to Integrations —> AWS

Click the blue Add AWS Account button.
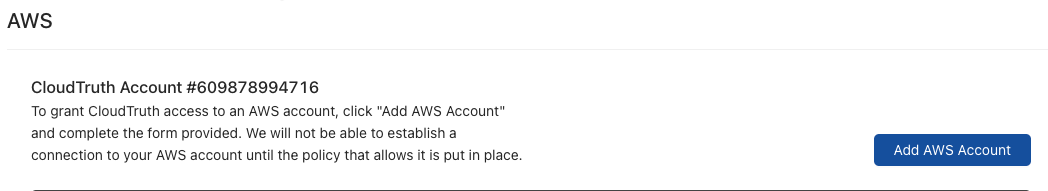
The Account Information for AWS will consist of:
- Your AWS account ID
- The AWS IAM role that you create for CloudTruth to have proper authorization to AWS
Once you add in the account ID and IAM role, you can choose what you want CloudTruth to have access to. The options are:
- S3 buckets
- AWS Secrets Manager
- AWS SSM
You can also choose whether you want CloudTruth to have access to write to S3, Secrets Manager, or SSM. By default, CloudTruth will have read access.
To set up the appropriate AWS IAM role policies for CloudTruth, read the integration doc.
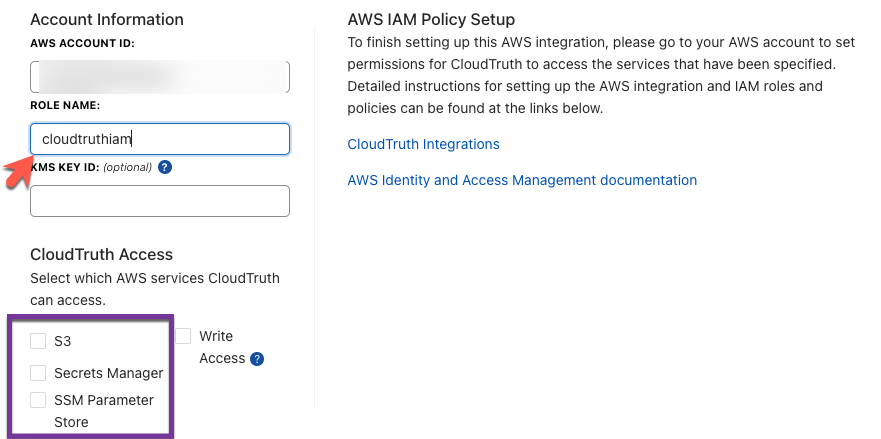
Once you save your configuration, CloudTruth will confirm that it has AWS access and display show Connected with a green checkmark.
The Azure Method
In this section, you’ll learn how to set up integration between CloudTruth and Azure Key Vault to read (or write) information from Key Vault.
On the CloudTruth homepage, go to Integrations —> Azure Key Vault
Click the blue Add Azure Key Vault button.
Choose your appropriate email account that has authorization to Azure.
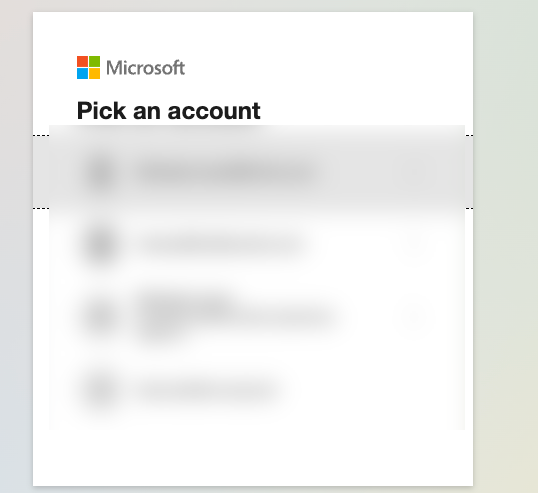
Add the name of the Key Vault that you want CloudTruth to have access to. You can also choose whether you want CloudTruth to have write access. The default is read access.
Wrapping Up
Integrating secrets, parameters, environment variables, and anything else that you can think of for your application is crucial. Having the ability to do it in one, centralized location is even more crucial. In today’s tech world, there’s a ton of configuration sprawl and typically far too many tools to choose from. Utilizing CloudTruth, you can make your life a bit easier and have one location to pull all configuration data from.
If you’d like to see a visual example of integrations, check out this video on setting up integrations with Azure.
{% video_player “embed_player” overrideable=False, type=’hsvideo2′, hide_playlist=True, viral_sharing=False, embed_button=False, autoplay=False, hidden_controls=False, loop=False, muted=False, full_width=False, width=’1920′, height=’1080′, player_id=’79520452756′, style=” %}
Join ‘The Pipeline’
Our bite-sized newsletter with DevSecOps industry tips and security alerts to increase pipeline velocity and system security.


