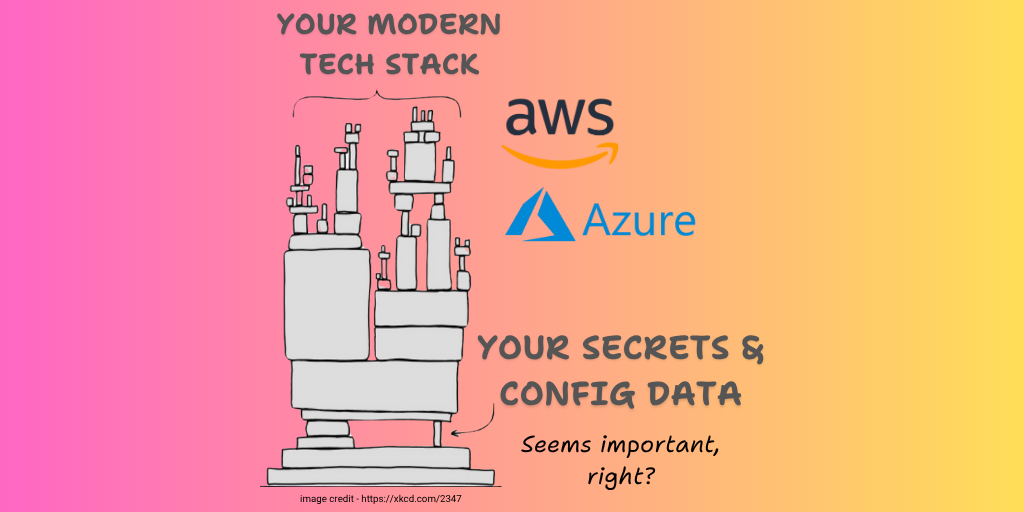
At the core of quality cloud, SaaS, and mobile app deployment is proper configuration management. Impacting your organization’s reliability, security, and costs, configuration management plays a major role in keeping your systems up and running. Yet despite everyone agreeing that reliability, security, and cost-efficiency are undeniably central pillars to any organization, many don’t take the time to iron out the kinks in their configurations. Read on to learn more about the impact cloud configuration complexity can have on your uptime, security, and cost controls.
A big reason why is because cloud configuration complexity is exploding, and even industry leaders are struggling to simplify it. Just last year, Facebook suffered a 6-hour outage as a result of a misconfiguration that affected 3.5 billion users. This equated to an estimated $6 billion in financial losses.
CenturyLink suffered an outage that affected 22 million customers in 39 states, which also prevented at least 886 calls to 911 not being delivered. Connectivity issues that resulted from a network misconfiguration error meant customers in the UK and Singapore had no connectivity for two days. As a result, CenturyLink was fined $16 million.
Suffice to say, failing to get a grip on configuration management can have incredibly detrimental repercussions on not only your business but the people you serve. To further emphasize the importance of proper configuration management, let’s look at some of the consequences of allowing configuration complexity to run amok.
Costly Downtime
As cloud configuration becomes increasingly distributed and decentralized, the number of settings touched by each deployment grows alongside it. This means more people interacting with configuration settings, which opens the door for misconfigurations.
One of the main fallouts from a misconfigured app or service is prolonged downtime. Research indicates that 75% of outages are the result of cloud misconfigurations, making them a major problem area for organizations that need to stay online, 24/7/365. No matter the size of your business or the industry you work in, downtime is disastrous for a number of reasons.
Clearly, the financial consequences of prolonged downtime speak for themselves, as highlighted in the examples above. 98% of organizations say a single hour of downtime costs them over $100,000, with 33% of those surveyed companies reporting that one hour of downtime costs them anywhere from $1M-5M.
But financial losses aren’t the only thing you need to worry about. Downtime damages your credibility and breaks trust with your customers. If one outage takes place, what’s to stop them from thinking that another outage won’t occur in the future?
Not only does downtime damage relationships with your existing customers, but it also can result in lost opportunities for prospective customers down the road. People will be quick to discuss your company’s outage online for the world to see, and the negative connotation associated with these incidents can be hard to shake off.
Security Exposure
Misconfigurations come in all shapes and sizes, but one of the more common examples pertains to bad parameter values. Let’s say one of your engineers unknowingly enters a typo or makes an uneducated mistake within a configuration. While the immediate effects may not be apparent, down the road these bad values can open the door for costly security breaches.
With close to 70% of all cloud security challenges stemming from misconfigurations, it’s evident that organizations need to button up their configuration management in order to avoid sensitive information falling into the wrong hands. This includes having sufficient oversight of secrets management to ensure all passwords, SSH keys, and certificates can be centrally managed and properly injected into the right pipelines.
Ultimately, the best way to avoid bad values and increase your security posture is to implement systems that validate configuration correctness with type checking, rules, and range validation. Working from a single record of configuration truth enables you to easily identify and diagnose configuration differences before they cause problems.
Decreased Velocity
While bad parameter values can open the door for security breaches, incomplete parameters or secrets can do the same, in addition to decreasing velocity.
When a new parameter or secret is added for a component but is not propagated or set correctly, your misconfigured apps are destined to fail. This problem usually manifests when trying to promote new features from lower-level environments to production.
When dev teams are working in tandem without a centralized DevOps group that orchestrates configuration workflows, adding new configuration values can often lead to configuration sprawl. The result? Decreased deployment velocity that leaves end-users upset and teams having to search multiple environments for where things went wrong.
Centralized cloud configuration solutions work to combat decreased velocity and ensure your teams are able to easily decouple configuration in a logical manner. As environments become increasingly complex, it’s important to give your teams the upper hand in making, tracking, and understanding changes across multiple environments. This minimizes the likelihood of decreased velocity and empowers your teams to solve problems faster.
Ready to Conquer Cloud Configuration Complexity?
Cloud configuration complexity has been creeping up on organizations for years, as modern configuration management momentum has been more reactive to the cloud’s current demands versus proactive to the road ahead. Homebrew tools can’t adapt quickly enough to the changing needs of the cloud, which is why many organizations embrace tools that combat distributed and decentralized configuration management.
Tools like CloudTruth.
Our platform unifies access and visibility into your organization’s infrastructure, application, and secrets configuration data. By leveraging CloudTruth’s API, CLI, and GUI, companies can manage their parameters, templates, environment variables, and secrets, all from one central location. Best of all, CloudTruth works to strengthen your existing tools and systems, meaning you won’t have to start your tech stack from scratch when you work with us.
Software developers and CloudOps teams rely on CloudTruth to ensure uptime, security, and team velocity. Learn more about our solutions or register for a free demo to see what CloudTruth can unlock for your teams.
Join ‘The Pipeline’
Our bite-sized newsletter with DevSecOps industry tips and security alerts to increase pipeline velocity and system security.